Gpgmail For Mac
If you are using Tiger and PGP Desktop, you may be on the brink of disaster so read on.
I’ll merely describe what happened to me so this is not fantasy.
Objective-C. Mac mini (Late 2012 or newer). iMac (Late 2012 or newer).
Let me describe where I was first.
My personal data security is not much of a concern. However, as a media and IT consultant, I keep a lot of confidential financial data belonging to my clients. That’s what I worry about. As PGP Corporation’s PGP Desktop is the only commercially supported and reasonably priced alternative I know, I’ve kept my data secured in the following ways:
Gmail free download - Gmail Notifier, Social for Gmail, App for Gmail, and many more programs. Gmail for mac free download - SysTools Mac Gmail Backup, Gmail, Gmail, and many more programs. GPGMail is a plug-in for Apple's Mail (on MacOS X 10.1) and MailViewer.app (on old MacOS X Server 1.x), providing a front-end to gpg for some operations. GPGMail extends Apple's Mail/MailViewer application and allows you to read and send PGP authenticated and/or encrypted messages. This short how-to guides users through the steps necessary to remove the popular open-source encryption plugin GPG Tools (GPGMail) from Apple Mail. It requires deleting a 'bundle' file used by the.
Pretty damning, huh? Indeed. And imagine losing access to part or even whole of that data.
Indeed that’s what happened when I upgraded to Leopard. (Of course I first made a bootable backup of my Tiger system using SuperDuper.) So in a way I’m always safe. Whatever working condition my system is, if Leopard does not work for me, I can at least boot back to Tiger from an external firewire disk and rescue my data.
As soon as I installed Leopard, I tried the latest PGP Desktop I have: 9.5. (I had lost hope of 9.6 because PGP disabled the vital mail bundle in 9.6 – without any prior warning!)
App itself: When I tried firing it up, nothing happened. The app seemed to be launching and then disappearing to oblivion. This app certainly was not going to work.
Disk: Tried to mount my current PGP Disk, same failure.
Mails: Since there was no mail bundle anymore, I had no way of accessing thousands of locked e-mails.
My passwords on PGP encrypted file. As I could not fire up PGP Desktop, that was a lost cause too.
Can you imagine the shock and anger?
Leopard was fantastic and I was being kept away from it for the sake of one badly done and badly supported application.
In the name of being fair, I must say I sustained my PGP communication still with the help of PGP. Now hold your breath: This is both exciting and useful: I fished in my hard disk for the oldest PGP Desktop I’ve ever bought: 8.1. Yes, it worked albeit partially. At least I was able to install it, import my keys, and use it to decrypt and encrypt text files!
So if you happen to have switched to Leopard and feeling miserable as I did, you might hunt for an 8.1 to relieve your pain partially.
I remain puzzled that 8.1 would work on OS X 10.5 but 9.6 would not. What’re the PGP Corporation guys smoking?
If you haven’t switched yet, please move on to the next few posts as you’ll find useful information to save you from a lot of headaches – and hopefully from PGP too. Dcs world for mac.
Also, I always keep a working PC complete with the latest PGP always by my side. Yes, dear PGP Corporation. I need you so much that I keep paying double every year for your software. I can almost visualize you rushing to your customer database to search for those buyers who regularly bought both versions Mac and PC. Don’t worry, I don’t buy them on behalf of the same client. Never.
Note: As of September 2018 (release 2018.4) GPG Mail is no longer a free plug-in for Apple Mail, and comes with a $25 fee for support for the current version.
Here we will look at how to send and receive encrypted and/or signed emails using Apple Mail with the GPGMail add-on.
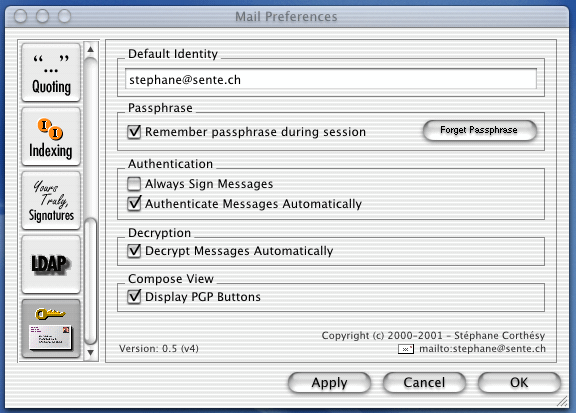
Contents
- Reading your first encrypted message
Before we begin…
If you have not already installed GPGTools you should go back and do that first before trying to carry out the instructions on this page.
Sending your first encrypted message
Note: At some points in this process you could be asked for the passphrase you used to create your key. This is to ensure you are the authorised user of the key.
To test that everything is working as it should be, you can send an encrypted message to yourself.
Open Mail and begin a new message addressed to yourself.
If Mail detects that it has a public key for the address you are sending to, then the lock icon just above the text of your message will appear black and will be selectable. Otherwise it will appear grey. Click the lock to close it as shown in the image below.
This indicates that the message will be encrypted. At the same time the OpenPGP icon at the top right of the window will turn green.
The icon to the right of the lock is for signing messages, we will come to this later.
You can now click Send and your message will be sent to you.
Reading your first encrypted message
You should find your encrypted message arrives quite quickly (it hasn’t had to go far!).
Click on it as you would any other message and you should see your message as below.
You might be asked to enter your passphrase when decrypting messages. You can always save your passphrase in the OS X keychain if you are confident your machine is secure and nobody could send messages on your behalf.
Your message will look very much like it did when you created it. They main thing to look for here is the line just above the message that says:
This shows that the email was encrypted when sent to you.
How do I know it was really encrypted?
This is a good question, and something you should check to satisfy yourself that it really was. Because the encryption is so well integrated with your email client, you never usually get to see the encrypted message.
To see the message as it was sent to the email servers, and also how it is stored on your machine:
Go to View > Message > Raw Source
A window will open to show you the message as it is stored on your computer.
We have excluded the message headers in the screen-shot above just to make the image smaller.
It is worth having a close look at this window to familiarise yourself with what is encrypted and what isn’t.
You will notice that sender, recipient and the subject line are not encrypted. This is necessary or it would not be possible to deliver your message (certainly in the case of recipient anyway). Do not put anything confidential in the subject of your emails.
However, the entire body of your message was encrypted and you will not see the text “This is my first encrypted message using Apple Mail, GPGMail and OpenPGP.” anywhere.
But all in all, it's still recommended for you.Features:. Make a program for mac. In some way, it means you need to give up some advanced features.
Note: Any attachments to your email (such as photographs or documents) will also be encoded with no further action on your part. Once they are decoded at the recipient end they will appear just as in an unencrypted message.
Sending your first signed message

Compose another message addressed to yourself similar to the one below.
This time, click the seal icon above and to the right of the body of your message so that is shows as selected (as below). This will tell Mail to sign the outgoing message. You can always send signed messages whether you have the public key of your recipients or not.
You can now click Send and your message will be sent to you.
If you don’t want the signed option to be enabled for each new message by default, there is a way to turn this off by entering a command in the Terminal application.
To launch the Terminal application go to Applications > Utilities and click on Terminal.
You can copy and paste the following command directly in to Terminal.
Reading your first signed message
When you receive your signed email, open it and you should see a window similar to the one below.
Here you will notice that under the messages headers and just above the content you see the line:
This tells you that the message was signed with the key for the email address mentioned.
If you click on the seal icon, a window like the one below appears to give you more information about the key used to sign the message.
If you receive signed emails from people whose public key you do not have, this may read “unknown key”. Keys have an ID number and Mail may try to download the relevant key from the key servers so that it can identify the sender. If it can find the key it will be added to your key chain.
As with the encrypted message, it is worth looking at the source code of the email so that you are aware of what signed emails look like in their “raw” format.
At first glance the source code looks similar to the encrypted message code. However, you will notice that the content of the message “This is my first signed message using Apple Mail, GPGMail and OpenPGP.” is now visible and not encrypted.
At the bottom of the email is a black of text starting with “—BEGIN PGP SIGNATURE___”. This is the OpenPGP signature that is used to verify the message is sent from you. In addition, the signature is based on the content of the message and so if the message is changed or tampered with before you read it the signature will be invalid and your email client will tell you this.
Note: You can encrypt and sign messages at the same time.
Start sending messages to people other than yourself
Now that you know how to encrypt and sign messages, you can start sending messages to everyone, right?
Well, perhaps not right away. There are a few things to consider first.
- You can sign messages with your own public key without needing the public keys of your recipients.
- Some people who use certain email clients or some webmail services will have problems reading any part of your signed messages.
- You can only encrypt messages to others if you have their public key.
- Others can only send encrypted messages to you if they have your public key.
Item 1 is not a problem, you already have your own key.
Gmail For Mac Mail
Item 2 can be a problem, and more information is available in our document Using OpenPGP – Some things you need to know.
Gmail For Mac Os
Items 3 and 4 are easily addressed by uploading public keys to a key server. This makes it very easy for others to find your public key so they can send you encrypted messages. Depending on the configuration, Mail with GPGMail will try to automatically download the public keys of people who send you signed and encrypted messages so that they are available for you to use. This can only happen if others have also uploaded their public keys to a key server.
Gpgmail For Macbook Air
If a key is not available from a key server, you will have to ask the person who owns that key to send it to you.
